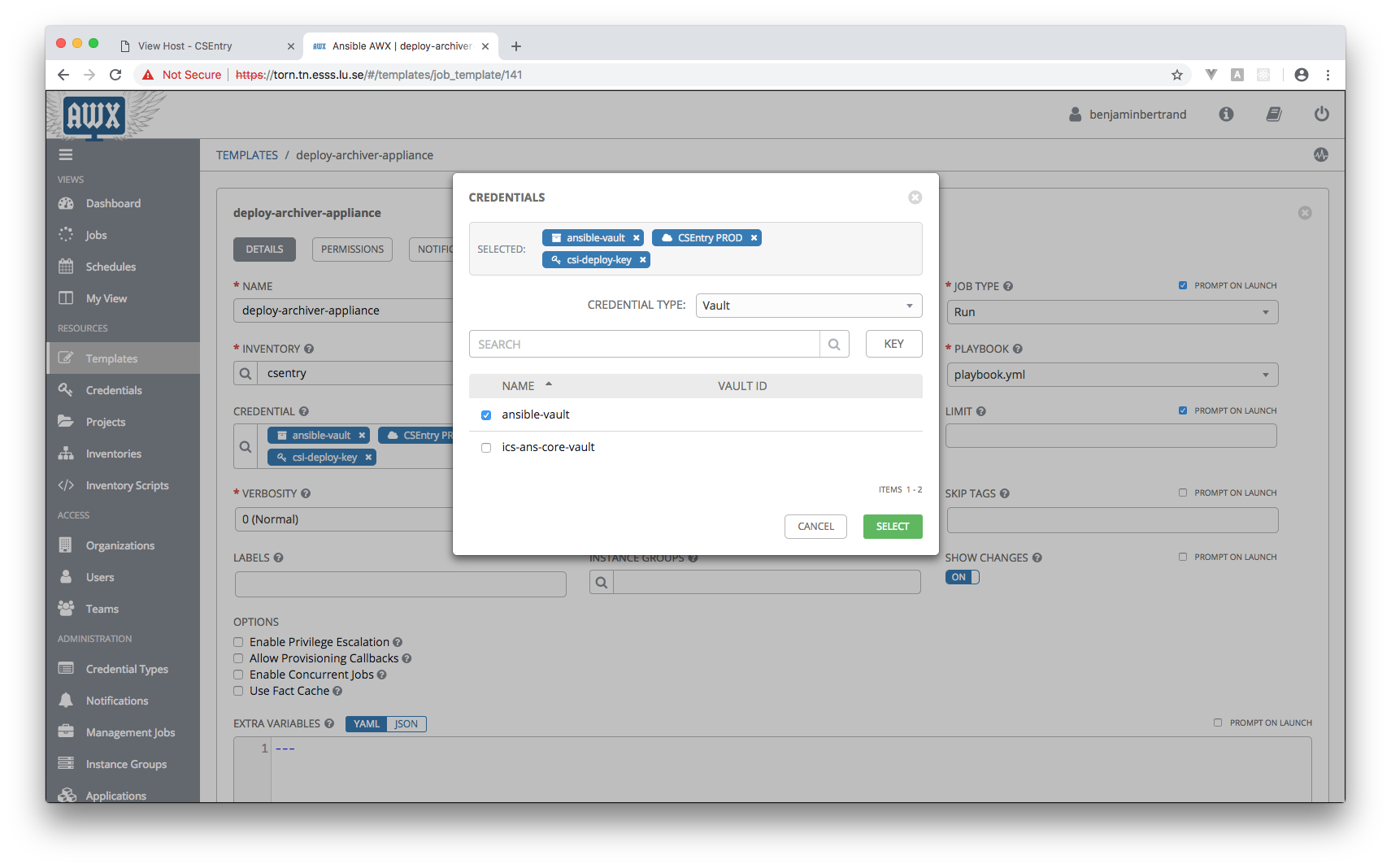
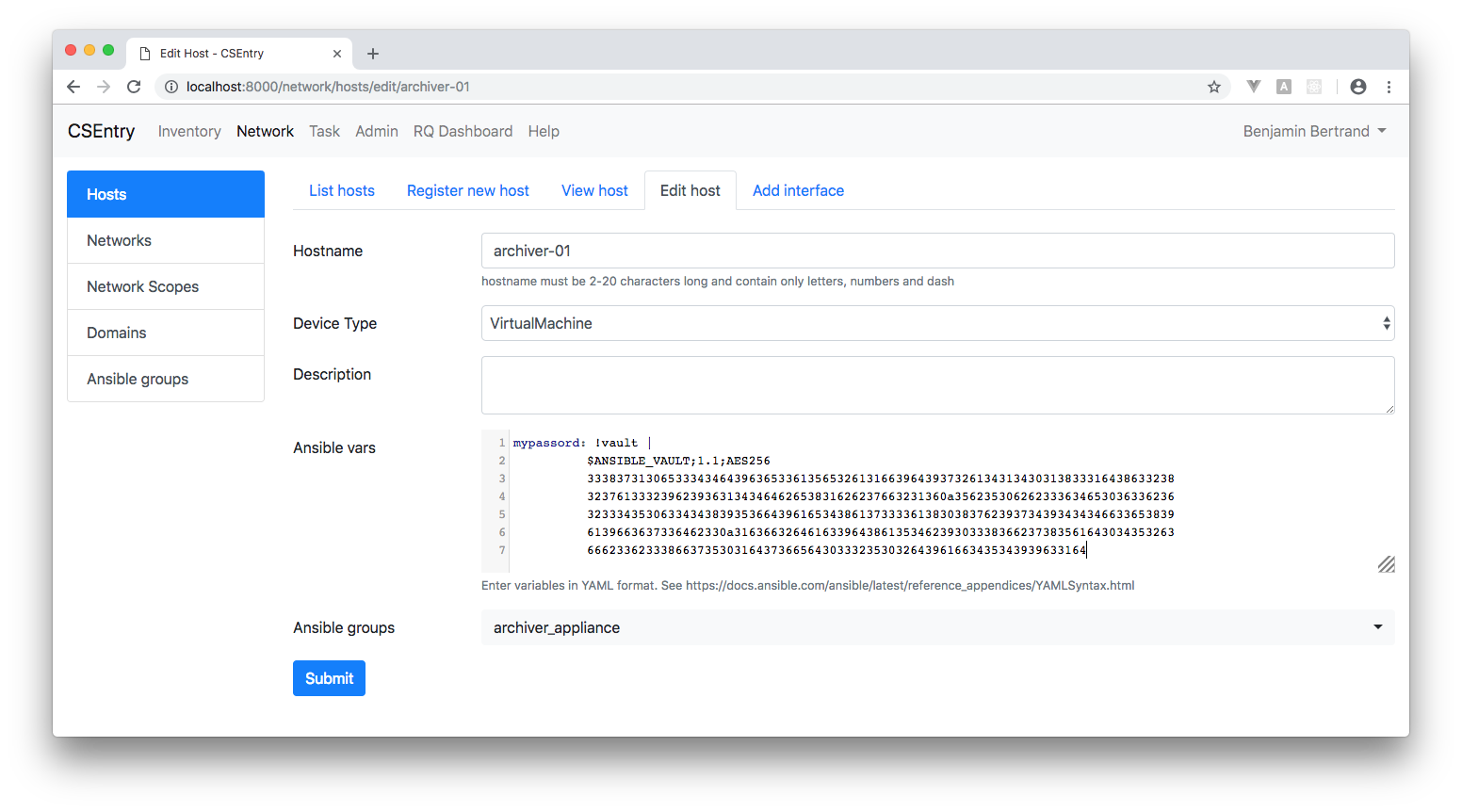
Add yaml constructor to support "!vault" tag
Allow to copy/paste the output of the "ansible-vault encrypt_string" command to CSEntry JIRA INFRA-544 #action In Progress
Showing
- app/fields.py 12 additions, 0 deletionsapp/fields.py
- docs/_static/ansible/awx_ansible_vault_credential.png 0 additions, 0 deletionsdocs/_static/ansible/awx_ansible_vault_credential.png
- docs/_static/ansible/enter_vault_variable.png 0 additions, 0 deletionsdocs/_static/ansible/enter_vault_variable.png
- docs/_static/ansible/saved_vault_variable.png 0 additions, 0 deletionsdocs/_static/ansible/saved_vault_variable.png
- docs/network.rst 39 additions, 0 deletionsdocs/network.rst
- tests/unit/test_fields.py 35 additions, 0 deletionstests/unit/test_fields.py
269 KiB
170 KiB
177 KiB
tests/unit/test_fields.py
0 → 100644